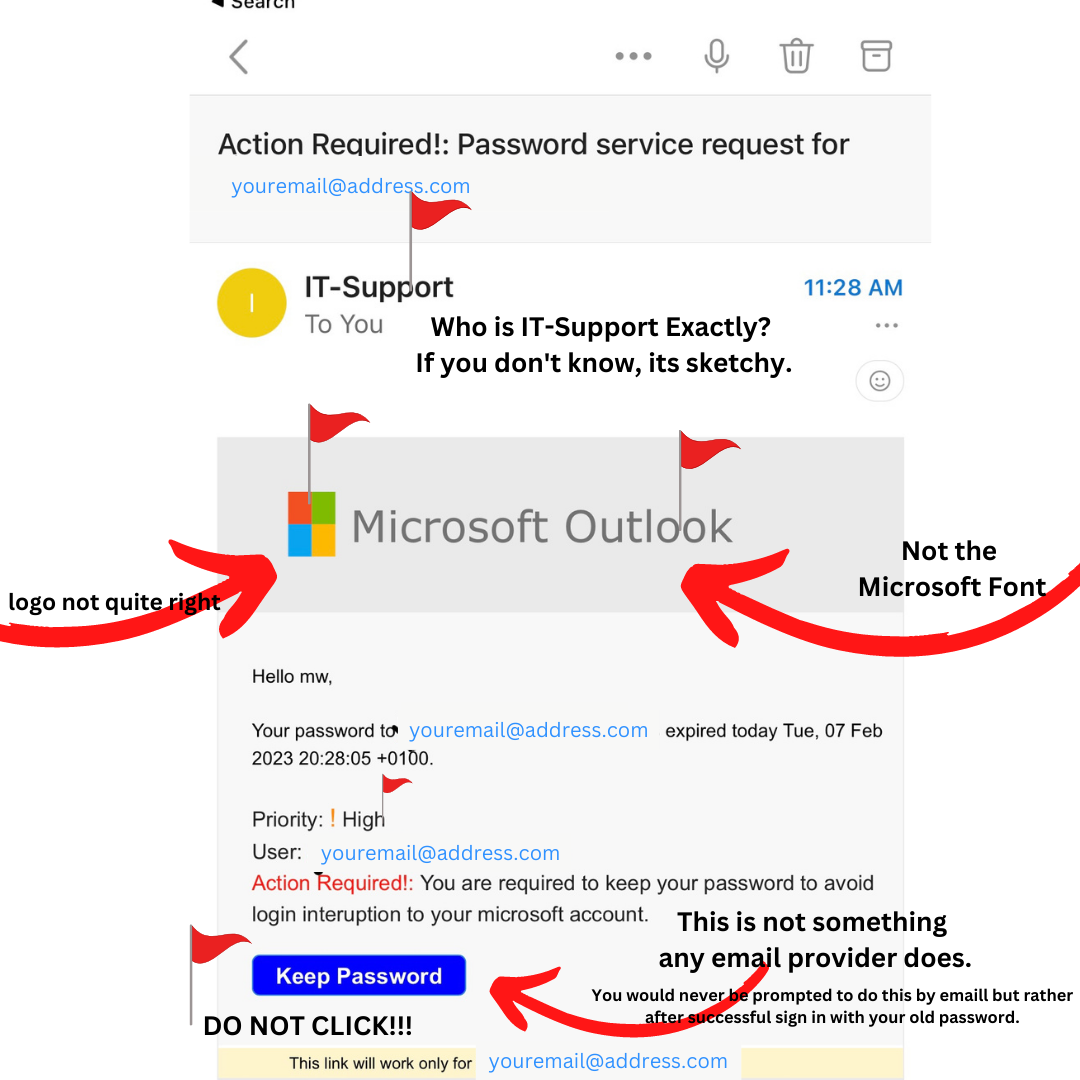
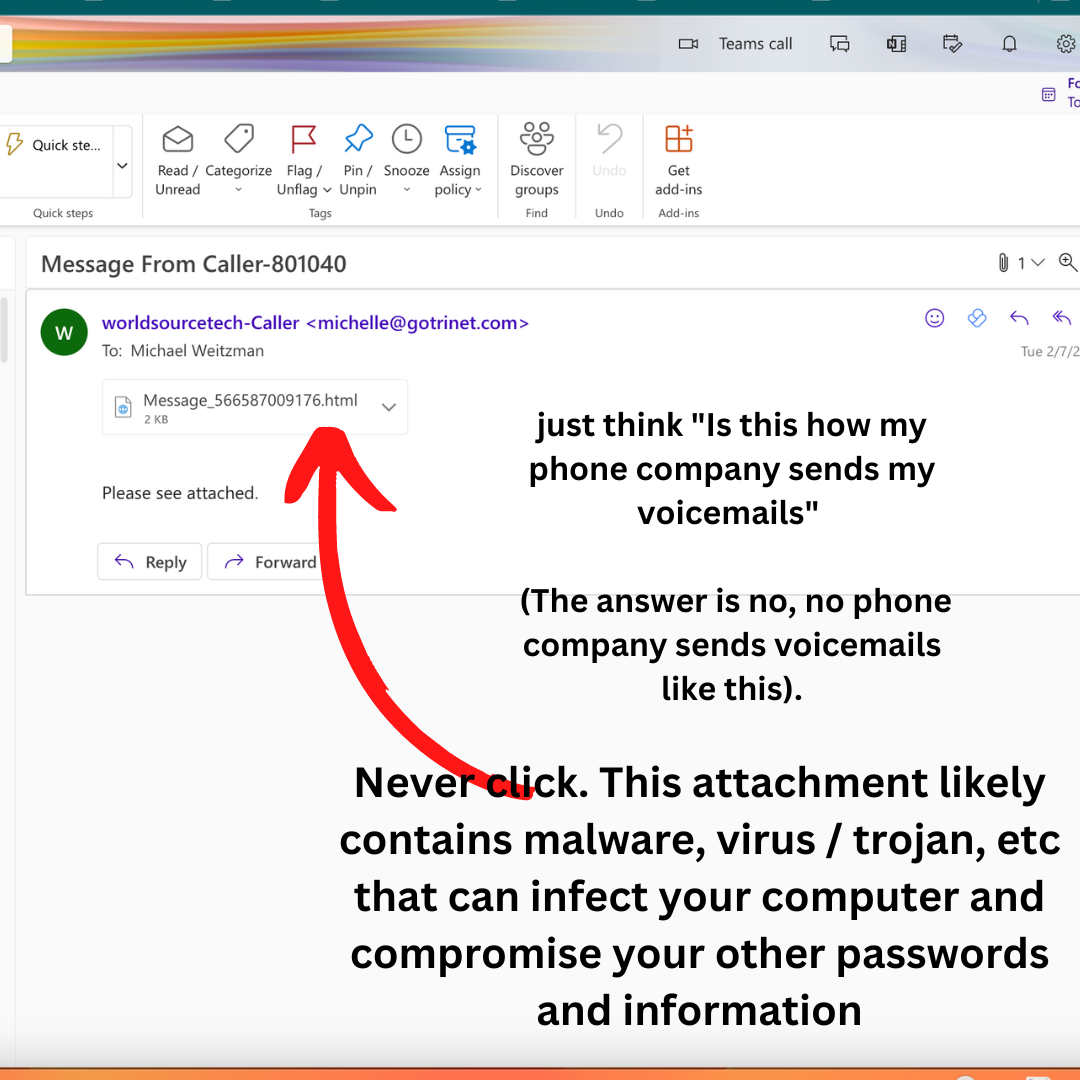
Email Phishing: In email phishing, scammers send emails that appear to be from a reputable source, such as a bank or online retailer, asking for personal information.
To avoid falling for this scam, DO NOT CLICK ON LINKS IN EMAILS THAT YOU'RE NOT EXPECTING, and always hover over the links to see the URL before clicking. Make sure that URL is the URL for a company you deal with, look for typos or subdomains that don't make sense.
The last part of the domain should be the company's URL. For example, verizon.scammer.com would be the scammer using verizon's name as a subdomain. but account.verizon.com would be Verizon's domain. Make sure you HOVER first to preview the link URL because the text can say one thing and be linked to another.
Additionally, be wary of emails that ask for personal information, as most companies will not request this information via email.